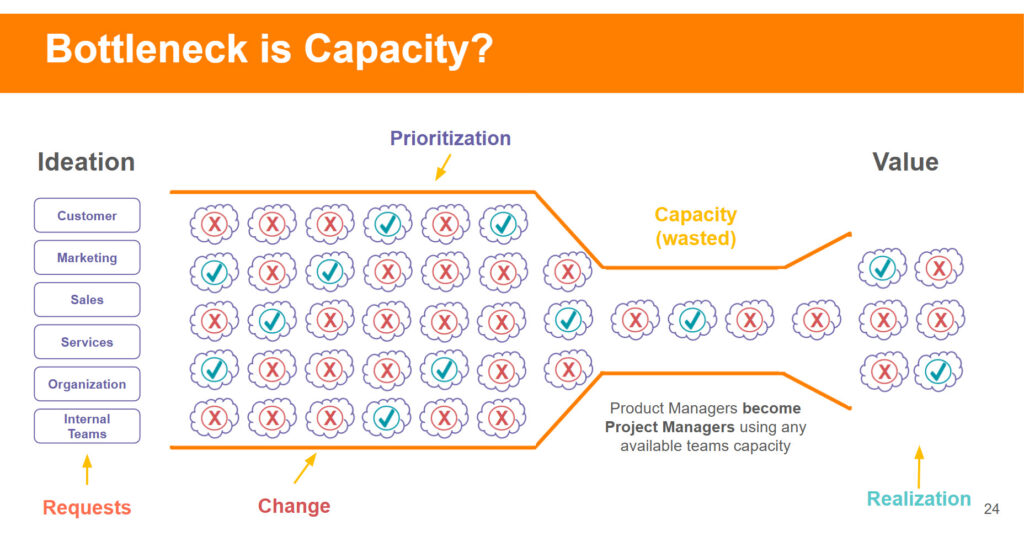
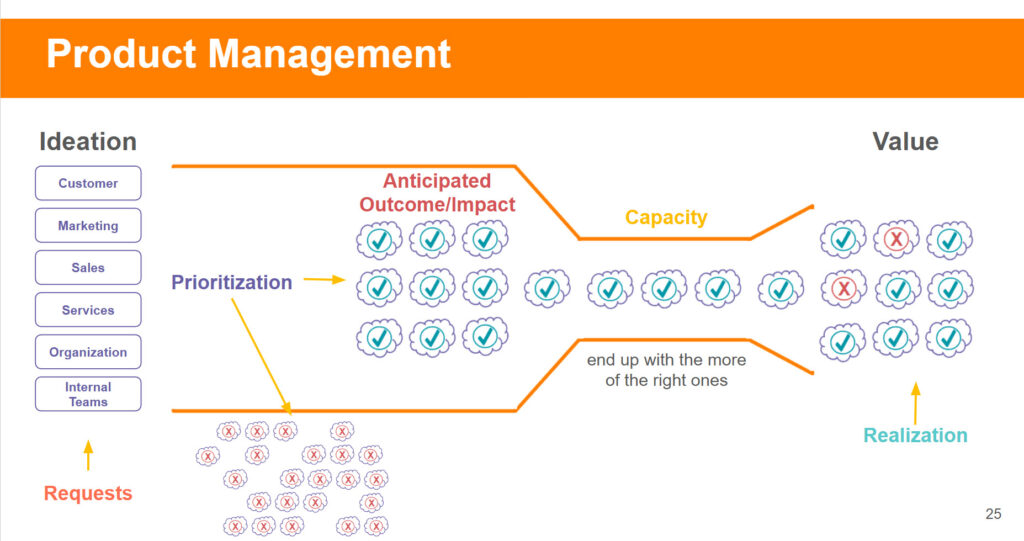
5 min read

In her recent article, Measuring What Matters: Using Outcome-Focused Metrics to Build High-Performing Teams in 2025 1, Leah Brown from IT Revolution, an industry-leading resource on digital transformation strategies, emphasizes prioritizing real business value over purely technical outputs. She highlights that truly effective value measurement requires:
- Clear alignment on strategic direction and goals
- Regular communication of value across stakeholders
- Built-in feedback loops to validate assumptions
- Focus on outcomes over outputs
- Willingness to adjust based on learning
This approach aligns with IT Revolution’s research, which has been instrumental in shaping modern software delivery practices. These principles align closely with my mission to bridge the gap between technology investments and business outcomes through better flow, business alignment, and leadership accountability.
A key challenge in many organizations is that software development and platform investments are often seen as black boxes, necessary costs disconnected from measurable business value. By structuring measurement around value streams and outcome-driven metrics, we can connect technology investments directly to business results and make the value of software delivery transparent.
Applying Value Stream Thinking to a Culture of Value Measurement
Shifting the organization’s focus to customer value streams is a key way to reinforce strategic alignment, feedback loops, and outcome-driven measurement.
When value streams are the core management approach:
- Customers get the immediate benefit of priority at the organizational level – In addition to internal teams optimizing for efficiency, the entire organization prioritizes work that directly improves customer outcomes.
- The organization becomes more responsive to customer needs and value creation, aligning outcomes over outputs. A value-driven operating model ensures that teams measure success not by what they produce but by how it improves customer experience, revenue, or retention.
- Problems surface earlier, and solutions are faster and more sustainable. Value streams highlight bottlenecks and inefficiencies in delivering customer value while supporting built-in feedback loops, ensuring that delays, hand-offs, and friction points are made visible before they become significant issues.
- Collaboration, continuous improvement, and problem-solving become natural outcomes – Instead of forcing teams into siloed KPIs, a value stream focus encourages alignment across departments, reducing hand-offs and friction, enabling faster decision-making, more iterative feedback, and fewer artificial constraints.
- There is a clear and transparent connection between work and value – In many organizations, software teams are seen as cost centers rather than strategic enablers. When work is structured around value streams, there is greater transparency into how investments in software development and platforms contribute to business goals. This alignment reinforces regular communication of value across stakeholders.
- All initiatives must be tied back to a customer or business metric. This principle directly supports outcome-driven measurement. By tying all work to business metrics, organizations avoid point optimizations (improving one team’s efficiency at the expense of customer value) and instead focus on work that improves a few critical metrics.
- Cross-company cultural initiatives become easier to implement – Many organizations struggle with broad transformation efforts because they are optimized for vertical silos, not horizontal value delivery. Value stream management connects teams across functions, making it easier to align priorities, drive enterprise-wide change, and improve strategic execution.
- Bureaucracy and process inefficiencies become visible – One of the most significant benefits of value stream-based measurement is that it exposes where excessive approvals, dependencies, and misaligned goals slow delivery. By tracking work across the value stream, organizations can see where bureaucracy blocks flow and make data-driven improvements.
Value Streams & Flow Metrics: Unclogging the Arteries of an Organization
In Value Stream Management conversations, the highway analogy regarding the greater volume on a highway, the more restricted cars travel (referring to work in progress or WIP), or if roadwork is slowing the flow is common (friction). Recently, I came across an analogy comparing Value Stream Management to clogged arteries. Most organizations operate like clogged arteries. Excessive hand-offs, approval processes, and misaligned priorities block value streams. Instead of measuring and improving flow, they optimize for vertical efficiency in isolated teams, much like focusing on individual organs rather than blood circulation.
- The heart keeps blood flowing freely in a healthy body, ensuring oxygen and nutrients reach every part of the system.
- Value Stream Management keeps work flowing freely in a healthy organization, ensuring value reaches customers and reducing delays.
However, many organizations suffer from congested workflows, unnecessary approvals, long hand-offs, and fragmented ownership, like arteries clogged with plaque leading to:
- Work stalling in queues instead of moving efficiently.
- Teams focus on local optimizations rather than system-wide flow.
- Decision-making being slowed by too much bureaucracy.
- Business leaders are unable to see where the real problems are.
Instead of waiting for a heart attack (a major failure or missed market opportunity), organizations should treat flow efficiency as a leading indicator of business health. Just as doctors track blood pressure and cholesterol to prevent heart disease, organizations should track Flow Metrics to avoid workflow breakdowns.
Value Streams as the Foundation of a Culture of Value Measurement
Building a true culture of value measurement requires structuring the entire organization around outcomes and customer value streams, not internal projects or siloed optimizations. Organizations can reinforce a culture of Outcome focus and Value Measurement using Value Stream Management.
- Start with Clear Alignment on Strategic Direction – Each value stream team should define or be clear on the expected outcomes before starting work.
- Regularly Communicate Value Across Stakeholders – Track progress using OKRs and periodic metric reports. Consistently evaluate performance to highlight progress, small achievements, or course corrections.
- Implement Feedback Loops to Validate Assumptions – Capture and reflect on Flow, DORA, and related Metrics across the entire value stream, not just engineering velocity.
- Focus on Outcomes, Not Just Outputs – Use Value Stream Thinking to ensure teams optimize for business results rather than just completing tasks.
- Be Willing to Adjust Based on Learning – If a team’s work isn’t improving a key customer metric, be willing to pivot and shift priorities based on real-world feedback.
- Make Technology Value Visible – Stop treating software and platform engineering as an invisible backend function. Instead, connect technology investments directly to business goals like revenue, customer retention, and agility.
Want to Go Deeper?
For further reading, check out these articles:
- From Good to Great: Shifting to Outcomes in 2025
- Why Value Stream Management and the Product Operating Model Matter
- Profitable Engineering: Linking Software Engineering to Business Results
Metrics
- Navigating the Digital Product Workflow Metrics Landscape: From DORA to Comprehensive Value Stream Management
- Finally, Metrics That Help: Boosting Productivity Through Improved Team Experience, Flow, and Bottlenecks
Let’s continue the conversation: how is your organization shifting from output tracking to actual business impact using value streams?
Poking Holes
I invite your perspective on my posts. What are your thoughts?.
Let’s talk: [email protected]
References
- Measuring What Matters: Using Outcome-Focused Metrics to Build High-Performing Teams in 2025, Leah Brown, IT Revolution, https://itrevolution.com/articles/measuring-what-matters-using-outcome-focused-metrics-to-build-high-performing-teams-in-2025/